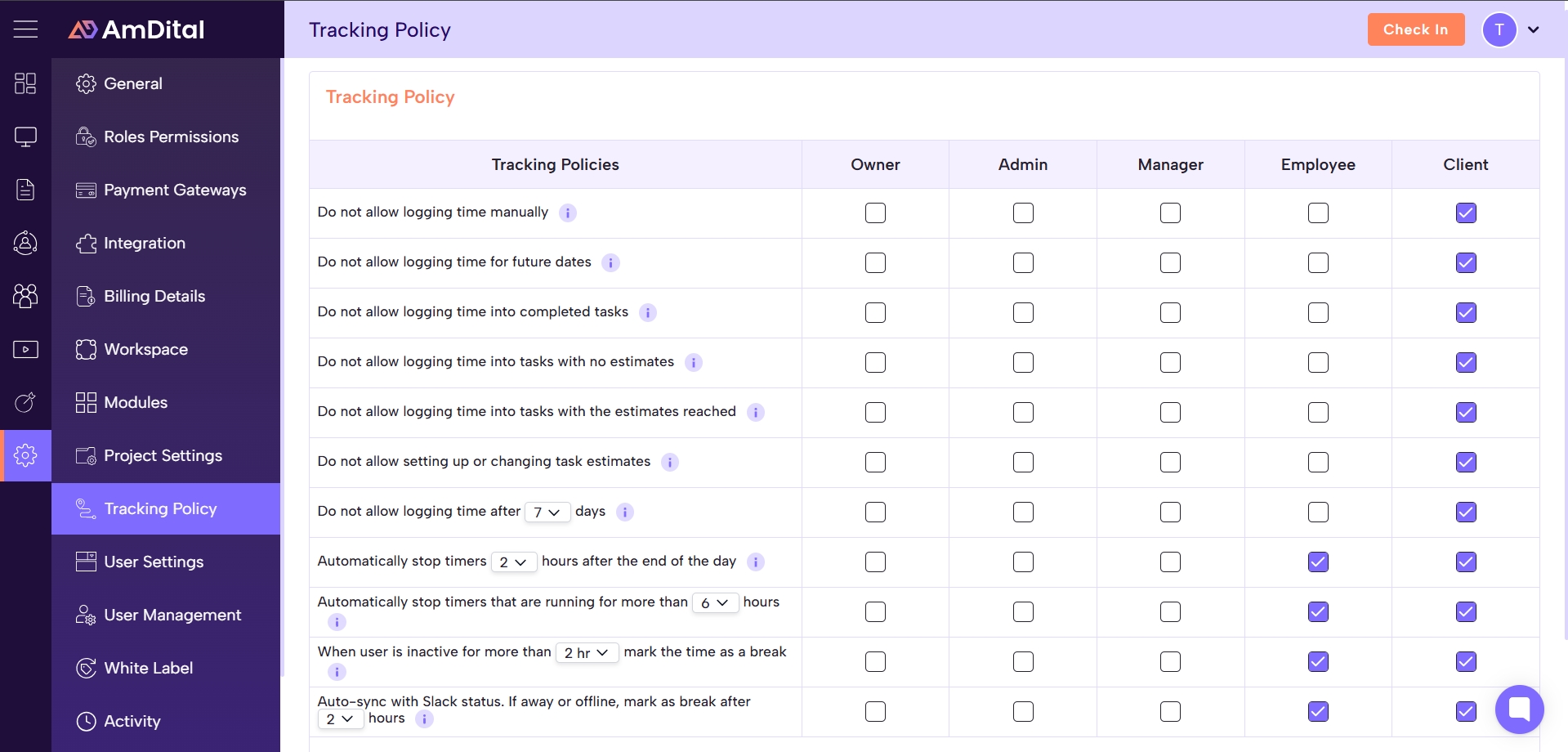
Enable/disable logging of certain actions (e.g. “delete record”, “task edit”) so that only relevant actions are tracked.
Retention period: decide how long logs/data are stored (e.g. 30 days, 1 year) for privacy and storage cost reasons.
User consent or privacy settings: for example, showing notices or allowing users to opt‐out of some non‑critical tracking.
Who can view the logs: typically only admins or audit roles.
Export / delete logs: ability to download logs or purge old logs.
Integration with external monitoring tools: sending logs to external SIEM tools or alerting platforms.